

Flag: Tornado!
Hurricane!
|
 |

[+] expand
|
 |
SoySauce Blueprint
This is the command and control code for soysauce.dll, graph is screen captured, rotated into perspective with photoshop, and some zoomed in close-ups of various details shown. Just messing around, but it's funny how close software resembles a microchip. Initial graph rendering was done w/ HBGary Responder using incremental layout, perspective and lighting effects were done with Photoshop CS2. The target is a malicious binary captured in the last couple of weeks.
|
[+] expand
|
 |
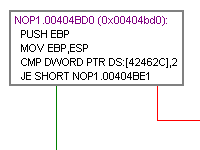
Immunity Debugger on the Run!
This screenshot shows Immunity Debugger rocking with NOP1.exe. You can see the Code flow graph of one the functions, a dump of the default heap and the execution of the Python Script that searches one of the chunks (from the command line).
Immunity Debugger is a powerful new way to write exploits, analyze malware, and reverse engineer binary files. It builds on a solid user interface with function graphing, the industry's first heap analysis tool built specifically for heap creation, and a large and well supported Python API for easy extensibility.
|

[+] expand
|
 |
Matt Pietrek - Book
Written by Matt Pietrek, this is one of the last elite-old school bible for would be reverse engineers, and also probably one of the most popular out-of-print. This book, unlike others, went into the smallest details of the new Windows 95 system, including descriptions of Memory, PE File Format, Debugging, Disassembly, Decompilation and many more low-level goodies.
One of my wet dreams was printing up the OCR'd PDF that circulated throughout the community, and I finally did it. Surprisingly enough, a great portion of this book is still relevant today, written almost 13 (!) years ago.
|

[+] expand
|
 |
Python +GPS +Google
This isn't at all reversing related, but it's time for a new screenshot in the imagery. This past February ralph and I drove from our home town of Austin to our old town of New Orleans to partake in the Mardi Gras festivities. We packed a healthy number of toys into his Jeep including:
- Dell 9300 laptop
- Power invertor
- Bluetooh enabled internet cellular modem
- Garmin GPS
- iPod
Ralph was driving and I was bored, so I started "gluing" some of our toys together using Python. First I connected the GPS to the laptop and wrote some code to read the GPS coordinates and heading off of the serial port. This was pretty easy to do. Then I thought, "hey, I have internet, why not real-time plot into Google Earth?". I was pleasantly surprised to discover that Google Earth is easy to control over the COM API. Next, I picked up some KML. Finally, I located an image of our vehicle online. Putting them all together we got what you see in the screenshot. A picture of the Jeep moving along in Google Earth in real-time. Better solutions exist of course, such as Earth Bridge. But that's not the point. All in all the script is under 200 lines of code, here it is for those of you who are interested:
|
[+] expand
|
 |
3D Studio Max Runtrace
Screenshot from a dynamic runtrace of control flow through the 3D Studio Max rendering server. I have a high resolution version measuring over 100 inches across. I took a snippit of the hi-res version and superimposed a zoom so that you can see the detail.
Black edges represent branches, red edges are calls. Originally I had blue edges representing returns but adding these caused extreme image layout/rendering times. Black blobs represent basic blocks, and addresses are visible at higher resolutions.
|
[+] expand
|
 |
4 Clicks to Fuzzing Hapiness
A screenshot of the upcoming "pathfinder" feature of Inspector. In the screenshot, it leverages the process freeze-snapshot-restore capability to re-play the program from a point directly after a packet has arrived from the network. The fuzzer mutates the buffer in-memory, eliminating the need to setup a client-server connection for each input test. Control and data flow is tracked downstream from the input point. You can see that the "packet" being processed by the target program is being randomly fault-injected. Of course this is seedable so the sequence can be reproduced. Fuzzer scripts are also an option, written in C#. Future versions will also include our AFR algorithm that mathematically derives the inputs required to uncover new control flows. Results are graphed at runtime, dynamically and collectively over the test for all iterations.
Not quite "put the binary in this side, advisory prints on the other (w/ your logo on the letterhead)" but about as close as we can get. More info on Inspector is available at the HBGary website.
|

[+] expand
|
 |
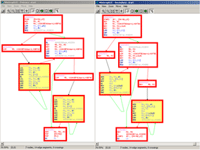
PaiMei - RE Framework
PaiMei is a reverse engineering framework consisting of multiple extensible components. The goal of the framework is to reduce the time from "idea" to prototype to a matter of minutes, instead of days. PaiMei is written entirely in Python and exposes at the highest level a debugger, a graph based binary abstraction and a set of utilities for accomplishing various repetitive tasks. The framework can essentially be thought of as a reverse engineer's swiss army knife and has already been proven effective for a wide range of both static and dynamic tasks such as: fuzzer assistance, code coverage tracking, data flow tracking and more. You can snag PaiMei from /downloads/details/208/PaiMei.
The expanded view is a screenshot from the PaiMei GUI, specifcally the pstalker code coverage tracking module being applied to pinpoint the code responsible for game logic behind Minesweeper.
The documentation for the framework is available online at: http://pedram.redhive.com/PaiMei/
Slides from the public release at RECON2006 are available from my respository: RECON2006-Amini.zip
|
[+] expand
|
 |
Cross Platform Diffing
This thumbnail/screenshot shows an excerpt from the comparison between Comwarrior.B and Comwarrior.C as calculated by Sabre Security's BinDiff. While B is compiled for standard ARM, C is compiled in thumb mode, which is pretty much the same as being compiled for a different CPU (thumb means that all instructions are different).
The amusing result is that even though the compilation is for a different platform, we still get roughly 61% of the functions matched. And the functions, which are clearly the same on the structural (e.g. flowgraph) - level, have completely different instructions, and manual inspection will confirm that these differing instructions end up doing the same.
You can manually verify this at here.
|

[+] expand
|
 |
Self Organizing Networks and Malware
This thumbnail/screenshot shows the resulting eyecandy from a Mathematica based analysis of a large collection of malware bots using Self Organizing Networks (SOM).
SOMs are simple neural networks which have the advantage of making clustering of high-dimensional data really easy. The initial scatterplot (see larger screenshot) was created using 3-dimensional vectors with the ImageBase, AddressOfEntryPoint members of the PE header and the first section's size. I ran that through the SOM which gave pretty nice clusters.
I went a bit further then and ran some code I wrote using pydasm which disassembles the binaries and gives me a 36-dimension vector (originally spits out a 6x6 matrix) representing specific characteristics and patterns within the code. I then run that data through the SOM code and again produced defined clusters. Not that surprising since this approach captures patterns in the code and most of those binaries share commons packers (UPX and the likes). Finally, I then went on making a 3D histogram by counting how many samples fell into each bucket (see larger screenshot). The two histograms are of the same data, the second plot is logarithmic though.
|
[+] expand
|
 |
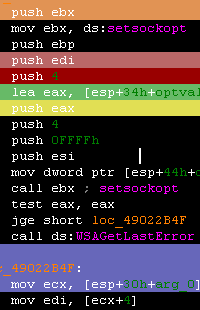
IDA Disassembly & Graph Coloring
This thumbnail/screenshot shows an excerpt from the IDA disassembly view after getting colored through a small IDC script that binds hotkeys (assign_color.idc) to routines that will ask for and apply desired colors.
The pGRAPH plug-in was updated as well to extract and display per node custom colors. Basic blocks are colored in the pGRAPH by the color of the first instruction in that block. The assign_color.idc IDC script is available in my repository.
|
[+] expand
|
 |
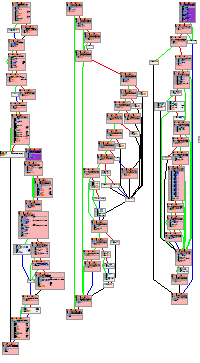
Process Stalker vs. MS05-030
This thumbnail/screenshot shows Pedram's Process Stalker vs the Microsoft Outlook Express NNTP Response Parsing Buffer Overflow Vulnerability addressed in MS05-030. The vulnerability is easily re-discovered in less than 30 minutes using the process stalking filter techniques. In this specific case, of the 20 highlighted nodes that process stalker determined as "interesting", the second one contained the actual vulnerability. (note: the screenshot shown is not the complete graph)
A complete article outlining the re-discovery process is available. Further information regarding downloads and documentation are available at the end of the article.
|
|
|
 |
|
There are 31,325 total registered users.
|
|

